This is one of the most path-breaking mechanisms in blockchain technology. Earlier decentralized peer-to-peer digital currency systems used to fail because of something called the “Byzantine General’s Problem”. The proof-of-work consensus system finally provided a solution to this problem.
What is the Byzantine General’s Problem?
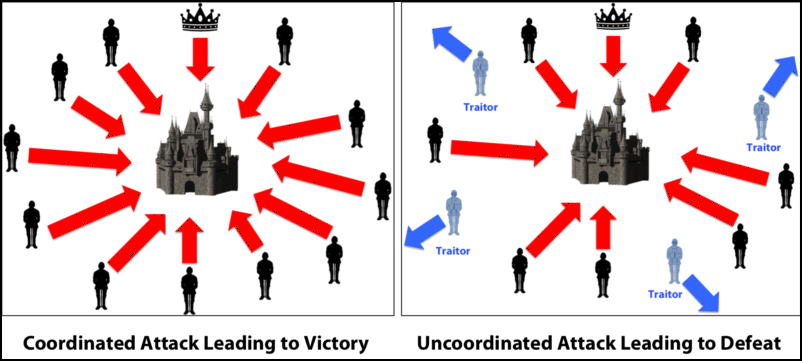
Image Courtesy: Medium
Ok so imagine that there is a group of Byzantine generals and they want to attack a city. They are facing two very distinct problems:
- The generals and their armies are very far apart so centralized authority is impossible, which makes coordinated attack very tough.
- The city has a huge army and the only way that they can win is if they all attack at once.
In order to make successful coordination, the armies on the left of the castle send a messenger to the armies on the right of the castle with a message that says “ATTACK WEDNESDAY.” However, suppose the armies on the right are not prepared for the attack and say, “NO. ATTACK FRIDAY” and send back the messenger through the city back to the armies on the left. This is where we face a problem. A number of things can happen to the poor messenger. He could get captured, compromised, killed and replaced with another messenger by the city. This would lead to the armies getting tampered with information which may result in an uncoordinated attack and defeat.
This has clear references to blockchain as well. The chain is a huge network; how can you possibly trust them? If you were sending someone 4 Ether from your wallet, how would you know for sure that someone in the network isn’t going to tamper with it and change 4 to 40 Ether?
Satoshi Nakamoto was able to bypass the Byzantine General’s problem by inventing the proof of work protocol. This is how it works. Suppose the army on the left want to send a message called “ATTACK MONDAY” to the army on the right, they are going to follow certain steps.
- Firstly, they will append a “nonce” (an arbitrary number that can be used just once) to the original text. The nonce can be any random hexadecimal value.
- After that, they hash the text appended with a nonce and see the result. Suppose, hypothetically speaking, the armies have decided to only share messages which, on hashing, gives a result which starts with 5 zeroes.
- If the hash conditions are satisfied, they will send the messenger with the hash of the message. If not, then they will keep on changing the value of the nonce randomly until they get the desired result. This action is extremely tedious and time-consuming and takes a lot of computation power.
- If the messenger does get caught by the city and the message is tampered with, according to hash function properties, the hash itself will get drastically changed. If the generals on the right side, see that the hashed message is not starting with the required amount of 0s then they can simply call off the attack.
However, there is a possible loophole.
No hash function is 100% collision-free. So what if the city gets the message, tampers with it and then accordingly change the nonce until they get the desired result which has the required number of 0s? This will be extremely time consuming but it is still possible. To counter this, the generals are going to use strength in numbers.
Suppose, instead of just one general on the left sending messages to one general on the right, there are 3 generals on the left who have to send a message to the ones on the right. In order to do that, they can make their own message and then hash the cumulative message and then append a nonce to the resulting hash and hash it again. This time, they want a message which starts with six 0s.
Obviously, this is going to be extremely time consuming, but this time, if the messenger does get caught by the city, the amount of time that they will take to tamper the cumulative message and then find the corresponding nonce for the hash will be infinitely more. It may even take years. So, eg. if instead of one messenger, the generals send multiple messengers, by the time the city is even halfway through the computation process they will get attacked and destroyed.
The generals on the right have it pretty easy. All they have to do is to append the message with the correct nonce that will be given to them, hash them, and see whether the hash matches or not. Hashing a string is very easy to do. That, in essence, is the process behind proof-of-work.
- The process behind finding the nonce for the appropriate hash target should be extremely difficult and time-consuming.
- However, the process of checking the result to see if no malpractice has been committed should be very simple.
Ok, so now you know what the fundamental principle behind mining is. Now let’s look at how it actually happens.
The Different Types of Mining
- CPU Mining: This is the most basic form of mining. The idea behind CPU mining is simple. Anyone, anywhere can use their computer to mine. While this method is not that applicable anymore, it’s a good entry point
- GPU Mining: Up next we have GPU mining. The GPU, or graphics processing unit, is a part of the video rendering system of a computer. The typical function of a GPU is to assist with the rendering of 3D graphics and visual effects so that the CPU doesn’t have to.The GPUs offer a far more stronger system for mining than the CPU. Some ASIC resistant coins like Monero are mined via GPU.Bitcoin/Ethereum used to be originally mined like this, however this became more and more difficult, as the difficulty increased. We will talk more about difficulty later on in the guide.
- FPGA Mining: FPGA or Field-Programmable Gate Array Mining is the next step from GPU mining. According to this article by Free Learner, FPGA “is a device that has a series of gate arrays (obviously) that create truth tables to calculate inputs from a data stream, and output a desired result. In industry you can use this to optimize an industry process, such as cutting 2x4s from a log, provide machine learning or even to perform DNA sequencing. FPGA’s excel at any task that can be done in a parallel process, such as a mining hash to create an output resulting in a successful hash, and if you’re lucky a successful block.”
- ASIC Mining: ASIC stands for Application-Specific Integrated Circuit and it was created for the specific purpose of mining Bitcoin and Litecoin. The idea of having machinery specifically designed for mining was ahead of its time, so much so that when KNCMiner launched their pre-orders for ASICs they received $25 million in orders in the first 5 hours. Bitcoin and Litecoin is now exclusively mined through ASICs. Bitmain recently released ASICs for Ethereum.
What is Proof of Stake?
So speaking of Proof of Stake (POS), what exactly does it mean and why is Ethereum going to move on to it? Let’s focus on the first part of the question for now.
Proof of stake will make the entire mining process virtual and replace miners with validators.
This is how the process will work:
- The validators will have to lock up some of their coins as stake.
- After that, they will start validating the blocks. Meaning, when they discover a block which they think can be added to the chain, they will validate it by placing a bet on it.
- If the block gets appended, then the validators will get a reward proportionate to their bets.
POS will make mining completely virtual and greatly reduce the wastage that will come about through POW.
Ethereum’s POS implementation is called the Casper protocol.
Why was Casper needed? Turns out, there is one big problem when it comes to POS implementation.
The Biggest Roadblock to Proof of Stake
Ethereum developers always planned to eventually move on to proof of stake, that was always their plan. However, before they could do so, they had to address one of the biggest flaws of proof of stake(POS).
Consider this scenario for a moment:
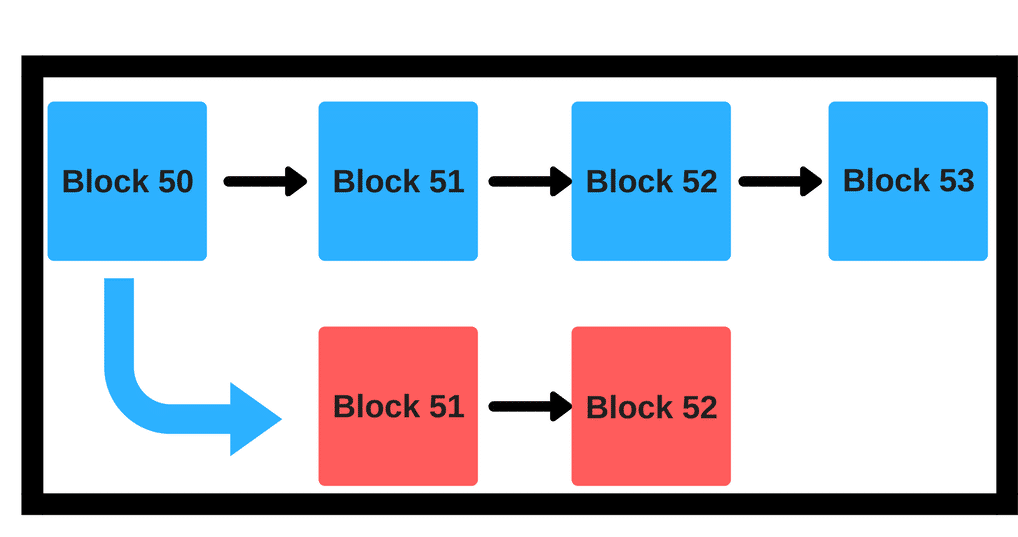
Suppose we have a situation like the one above. There are a main blue chain and a red chain which sort of branches from the main itself. What is there to stop a malicious miner from mining on the red blocks and force a hard fork?
In a proof-of-work(POW) system, this risk can be mitigated.
Suppose malicious miner Alice wants to mine on the red chain. Even if she dedicates all of her hash power to it, she won’t get any other miner to join her on the new chain. Everyone else will still continue to mine on the blue chain because it is more profitable and risk-free to mine on the longer chain.
Now remember, POW is extremely expensive resource-wise.
It makes no sense for a miner to waste so much resource on a block that will be rejected by the network anyway. Hence chain splits are avoided in a proof of work system because of the amount of money that the attacker will have to waste.
However, things look a little different when you bring in POS.
If you are a validator, then you can simply put your money in both the red chain and blue chain without any fear of repercussion at all. No matter what happens, you will always win and have nothing to lose, despite how malicious your actions may be.
This is called the “Nothing at Stake” problem, and this is something that Ethereum had to address.
They needed a protocol which could implement POS and mitigate the “Nothing at Stake” problem.
Enter Casper
Casper is the POS protocol that Ethereum has chosen to go with. While there has been an entire team busy creating it, Vlad Zamfir is often credited as being the “Face of Casper”.
Image Credit: Blocknomi.
So how is Casper different from other Proof of Stake protocols?
Casper has implemented a process by which they can punish all malicious elements. This is how POS under Casper would work:
- The validators stake a portion of their Ethers as stake.
- After that, they will start validating the blocks. Meaning, when they discover a block which they think can be added to the chain, they will validate it by placing a bet on it.
- If the block gets appended, then the validators will get a reward proportionate to their bets.
- However, if a validator acts in a malicious manner and tries to do a “nothing at stake”, they will immediately be reprimanded and all of their stake is going to get slashed.
As you can see, Casper is designed to work in a trustless system and be more Byzantine Fault Tolerant.
Anyone who acts in a malicious/Byzantine manner will get immediately punished by having their stake slashed off. This is where it differs from most other POS protocols. Malicious elements have something to lose so it is impossible for there to be nothing at stake.
This is not the only place where Casper punishes the validators.
As Hudson James and Joris Bontje note in their answers in “StackExchange”, Casper designs harsher incentives in order to guarantee network security, including punishing miners who go offline, unintentionally or not.
This means that validators will have to be careful about their node uptime. Carelessness or laziness will lead to them losing their stake. This property reduces censorship of transactions and overall availability.
Along with all that, the “slashing” property also lends casper a distinct edge over normal proof of work protocols.
Let’s bring back our chain diagram again:

In a proof of work protocol, it doesn’t matter whether a miner mined on the blue chain or the red chain. Both the honest and the malicious miner would have spent the same amount of resources.
In Casper, however, if an honest validator mines on the blue chain then they would get reward proportionate to their bet, however, a malicious miner will get their stake slashed off for betting on the red chain.
Ok so that’s all well and good but how is Ethereum going to make sure that miners will move on from POW to POS?
They plan to do that via a difficulty time bomb.
What is The Difficulty Time Bomb?
What is there to incentivize the miners to move from a proof-of-work protocol to a proof-of-stake protocol?
Miners buy thousands of dollars’ worth of equipment so that they can mine for blocks. The moment POS comes on board; all that equipment becomes worthless. Imagine spending so much money and having super intricate pools set up, and all that becoming completely useless.
If that is the case, then what is there to stop the miners from staying on the old proof-of-work chain and continue mining on it? This will, in essence, create three Ethereum coins: Ethereum Classic, Ethereum Proof-of-work, and Ethereum Proof-of-stake. That is going to be an absolute nightmare.
Not only will that greatly decrease the economic value and credibility of Ethereum, it is also going to dilute the hash rate of the overall chain which can make it vulnerable to hacker attacks.
In order to make sure that there is a proper incentive to miners to join the new chain, the Ethereum developers introduced the difficulty time bomb. The time bomb was introduced on 7th September 2015. To understand how the difficulty time bomb works, it is important to understand how difficult and mining works.
What is difficulty and how does it work?
The concept of difficulty started with bitcoin. When bitcoin was first introduced, mining was extremely simple and anybody could do it using their PC. However, as bitcoin got more and more popular the number of miners on the network increased. This raised a very real possibility of miners going out of control and mining out all the remaining bitcoins in the space of a year. Satoshi Nakamoto envisioned this happening and hence introduced the “difficulty” system.
The difficulty system works like this: Miners spend their computational power to solve cryptographic puzzles. The way they do that is that they randomly append a random string (called nonce) to the hash of the block and then they hash the whole string. If the resulting number is less than a particular fixed number, then it is considered to be successful and the new block is added to the blockchain. Finding this “nonce” is extremely difficult and random and that is the heart of all mining.
If we were to recap the whole process, then this is what it would look like:
- The hash of the contents of the new block is taken.
- A nonce (random string) is appended to the hash.
- The new string is hashed again.
- The final hash is then compared to the difficulty level and seen whether it’s actually less than that or not.
- If not, then the nonce is changed and the process repeats again.
- If yes, then the block is added to the chain and the public ledger is updated and alerted of the addition.
- The miners responsible for this given the block reward.
The difficulty is adjusted every 2016th block.
The difficulty level is directly proportional to the rate at which the blocks are being mined. Bitcoin has an average block time of 10 mins.
If the block time goes below that, then the difficulty level is increased, if it goes up, then the difficulty time decreases. This is done to make sure that the block time of bitcoin stays ~10 mins.
This is basically how bitcoin mining works and Ethereum follows the same protocol as well, the difference being that a block is mined every 15 seconds in Ethereum.
Following graph shows the increasing difficulty in Ethereum:
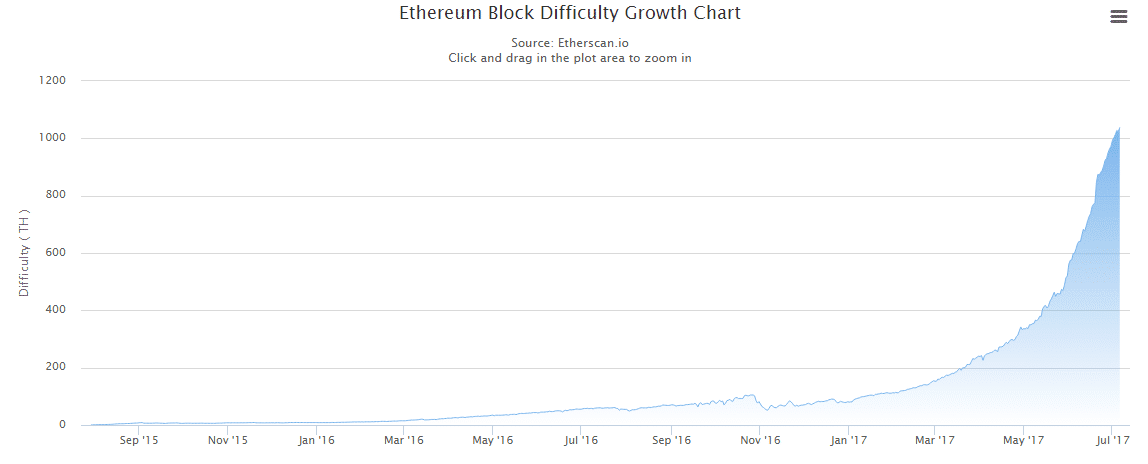
So what will the difficulty time bomb do?
The difficulty bomb will exponentially increase the difficulty so much so that mining will become impossible.
Like we have said before, the difficulty level adjusts according to the rate at which the blocks are being mined. The Ethereum difficulty adjustment algorithm looks like this:
block_diff = parent_diff + parent_diff // 2048 * max(1 – (block_timestamp – parent_timestamp) // 10, -99) + int(2**((block.number // 100000) – 2))
(In here “//” is the division operator such that 6//2 = 3 and 9//2 = 4.)
So, let’s understand what that basically means in plain English:
Block_timestap = the time at which the block was mined.
Parent_timestamp = the time at which the parent block aka the block before this was mined.
- If (block_timestamp – parent_timestamp) < 10 seconds then a factor of “parent_diff // 2048 * 1” is added to the difficulty.
- If (block_timestamp – parent_timestamp) is between 10-19 seconds then the difficulty is kept the same.
- If (block_timestamp – parent_timestamp) > 20 seconds then the difficulty is reduced by “parent_diff // 2048 * -1” to a maximum of “parent_diff // 2048 * -99”.
This is how the difficulty adjustment algorithm worked in the Homestead version of Ethereum. The idea is to keep the block time ~15 seconds.
So, what the difficulty bomb is going to do is that it will increase the difficulty by such an exponential amount without adjusting it that it will take more and more time to solve the cryptographic puzzles. Eventually it will become near impossible to mine on the chain. This phenomenon is called the “Ethereum Ice Age”, the time all mining POW style becomes impossible.
When this happens, the miners will have no option BUT to go the new Ethereum chain which has Proof-Of-Stake on it.
Alright, so why is this desired? What are the problems that we are facing with Proof of Work that Proof of Stake is looking to solve?
Why POS is Needed over POW?
There are several advantages of implementing proof-of-stake. They can all be broadly listed down among the following categories. (Big shoutout to Jon Choi and his article).
- Helps achieve decentralization.
- Energy efficiency.
- Economic security.
- Scaling.
- Transition to POS.
Achieving Decentralisation
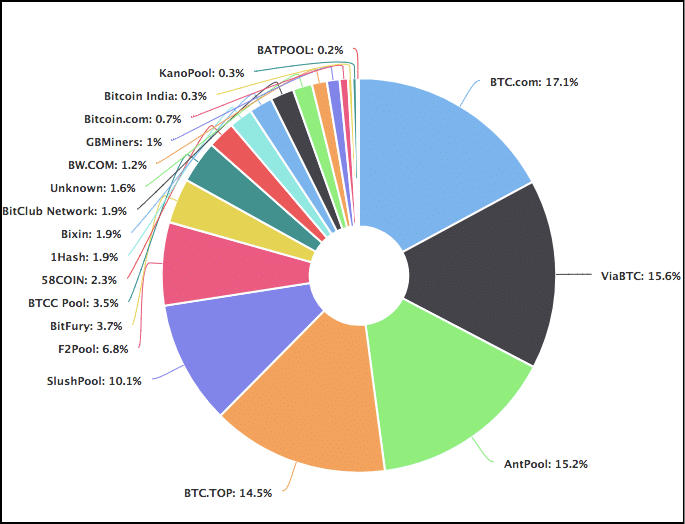
As we have seen above, POW protocols are not really decentralization friendly anymore. Let’s check out the hashrate distribution chart for bitcoin :
And here is the hashrate distribution of the mining pools in Ethereum:
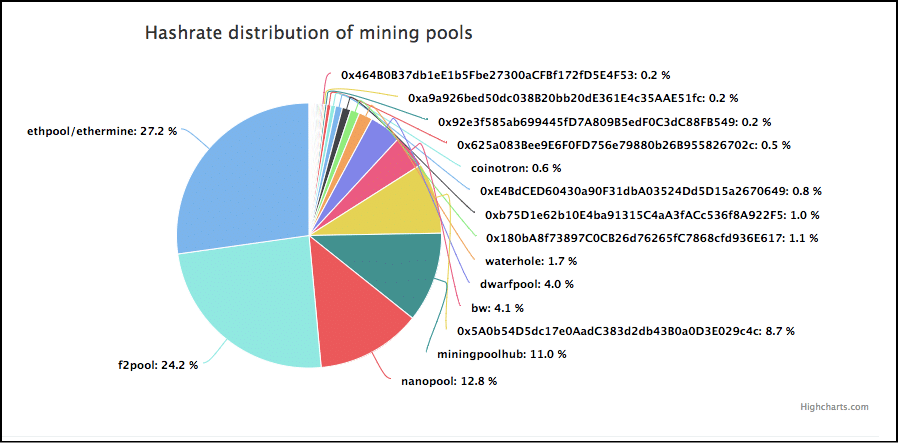
Image Courtesy: Etherchain.org
As you can see, majority of the hashrate is concentrated within some specific pools and this means that no matter what happens, they will always have a better chance of mining blocks and obtaining rewards than anyone else.
Because they can obtain more money, they can therefore afford better and faster ASICs. This basically means, no matter what happens, big mining pools will always have an edge over individuals and smaller pools. In other words, the rich will always get richer.
Proof-of-stake makes this completely irrelevant by making mining completely virtual. However, that’s not the only way POS mitigates the effects of centralization. In order to understand that, first we need to know what “Economies of Scale” means. (Thank ACDCLeadership youtube channel for the data).
When it comes to production, there are two kinds:
- Short Run production.
- Long Run production.
In the short run production, at least of the input resources are fixed. Consider a small-time pizzeria which has only one oven. It doesn’t matter if they have to produce 1 pizza of 25, there is the only oven that they can use to create those pizzas.
In a long run production, all the resources are variable, and this is where economies of scale come in.
So, in a long run production where the quantity of the input resources is variable, what happens if you double the input? There are only three outcomes to this particular scenario. We call this “returns to scale”.
- The output more than doubles. Meaning there is an increasing return to scale.
- The output doubles. Meaning there is a fixed return to scale.
- The output does not double. Meaning there is decreasing returns to scale.
The following will show you a graphical representation of economies of scale.
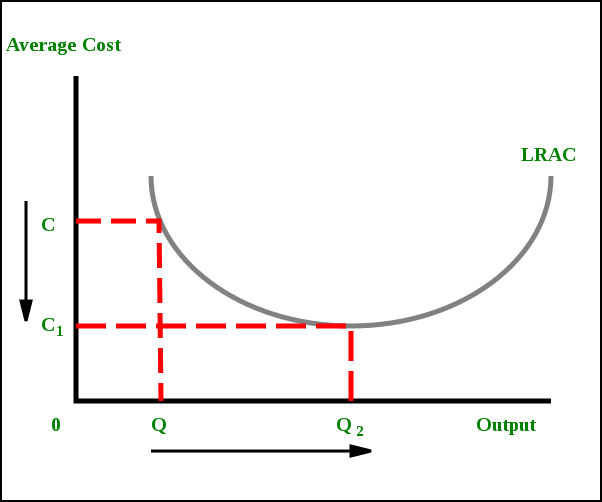
Image Courtesy: Wikipedia
What exactly is going on here?
When the production is increased from Q to Q2, the overall cost of the production goes down from C to C1. This is called Economies of scale.
After that, it evens out for a bit. This is where you get constant returns to scale.
And then when you go beyond that, the cost increases as you increase the output beyond Q2.
What this means is that large corporations can decrease the average cost of their products by increasing the number of their outputs! (Till a limit)
In a sense…more is less!
Let’s take a real-world example of that.
A small-time baker’s initial costs will obviously be less than a big baking company’s because the company will have to invest in a lot of machinery. However, over the long run, the average cost of each and every loaf of bread will be much lesser for the company than it is for the baker.
Ok, all this is fine, but how does it apply to mining pools?
Quite like big corporations, larger mining pools can decrease the cost of their input resources by:
- Amortizing a fixed cost over a larger operation.
- Having bargaining power by operating as a larger entity.
What this basically means is, a large influential mining pool can, dollar-for-dollar, generate more hash-rate than other pool even if they spend the same amount of money.
This problem is completely mitigated in proof-of-stake because of one simple reason. In POS you invest a stake. You can’t simply pool together and make your stake more valuable dollar-for-dollar. At the end of the day, 1 dollar = 1 dollar. Economies of scale don’t work here.
Energy Efficiency
The biggest problem of Proof-of-work is the energy wastage. The worst part is that it is energy wastage for the sake of energy wastage. Bitcoin, in particular, is voracious in its appetite for energy. Check this out:
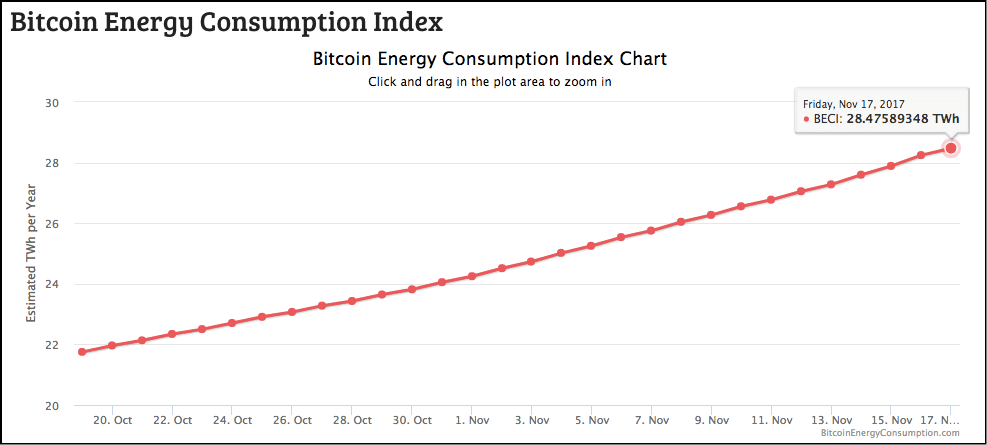
Image Courtesy: Digicnomist
How about some more numbers (courtesy Digicmonist)
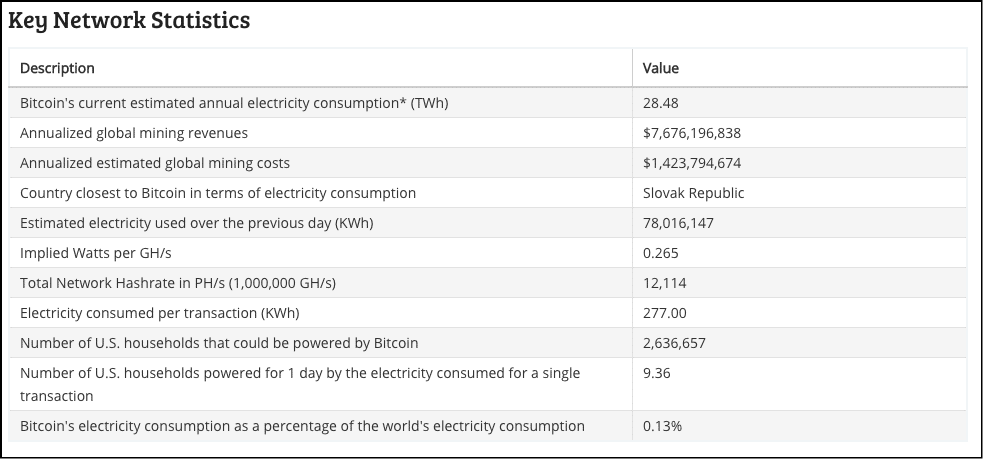
There are two numbers that you should focus on:
The annual global mining costs of bitcoin is $1,423,794,674.
Bitcoin alone annually consumes 28.48 TWh worth of electricity. The country of Ecuador consumed around 21 TWh!
In fact, let’s compare bitcoin’s energy consumption when compared to some countries:
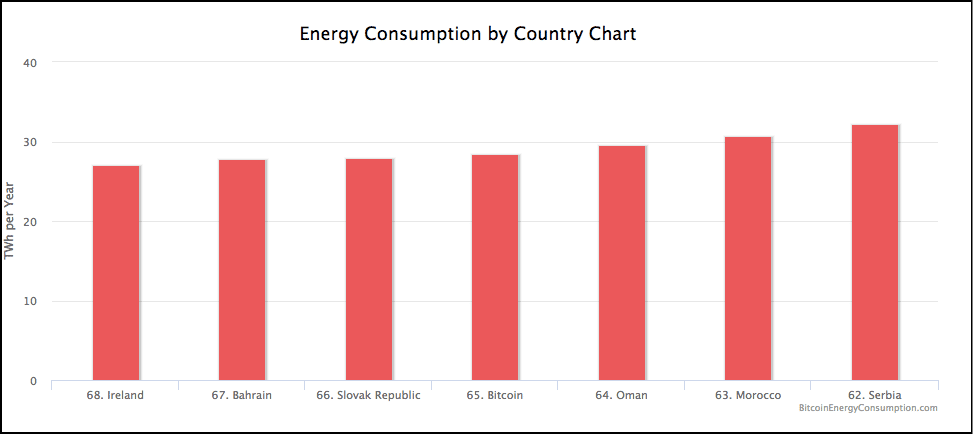
Bitcoin consumes more power than Ireland, Bahrain and Slovak Republic!
Ok, let’s even the playing field.
What if we compare Bitcoin to other payment systems? Say…Visa.
How does the power consumption of bitcoin compare to that of visa?
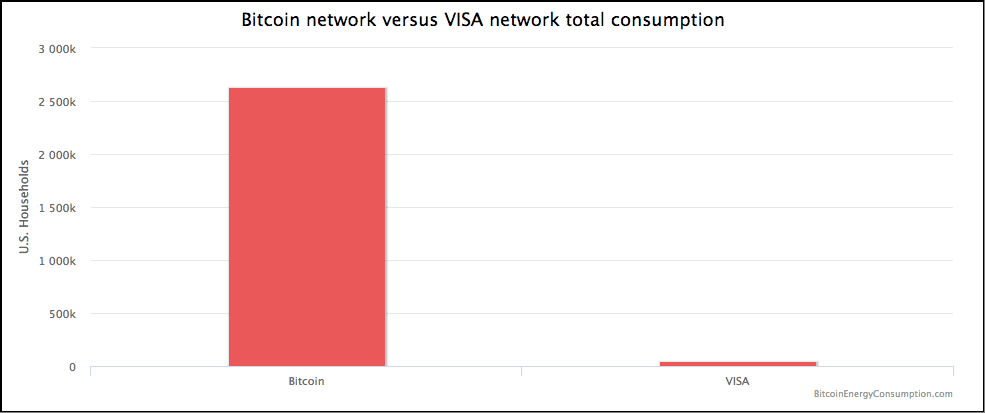
Yeah…not good.
So it is obvious that bitcoin eats a lot of power, and there is a lot of money spent on the resources. However, what about the external costs? The effect that this amount of power consumption has on the environment must be immense.
While there is no doubt that bitcoin and POW has made a lot of positive social changes, we should at least see what a large scale POS system can do and whether it work just as well without consuming so much power.
Economic Security
The biggest advantage that POS, and especially Casper, has is its economic security. Think about this, suppose you are a validator and you have your own money stored up as a stake in the network. It is in your own interests to act in the best interest of the network. Why would you act maliciously knowing that there is a huge part of your stake which can be slashed away and taken over if you do?
Why would you attack a network and harm the coin’s value when you have so much of your currency locked up in it?
Also, this “slashing effect” removes the chance of a “spawn camping attack” as Vitalik coins it:
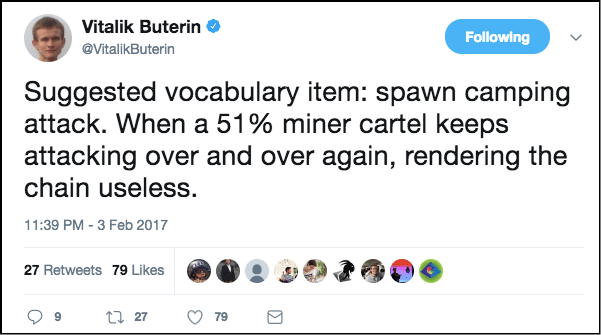
Image Courtesy: Vitalik Buterin Twitter.
Spawn attacks can be prevented in POS by the simple fact that just one attack will lead to the slashing and removal of the invested stake. And if you don’t have any stake invested you cannot take part in POS validating.
Scaling
The most obvious way that POS is going to help scalability is by enabling sharding.
As Vlad Zamfir says, sharding with POW is not impossible, but it is hard.
Sharding is a term that has been taken from database systems. Let’s see what sharding means with respect to database. Suppose you have a huge bulky database for your website. Having a bulky database not only makes searching for data slower, but it also hinders your scalability. So, what do you do in this case?
What if you do a horizontal partition on your data and turn them into smaller tables and store them on different database servers?
Image courtesy: Dzone
Like so?
Now, you might be asking, why a horizontal partition and not a vertical partition? That is because of the way tables are designed:
Consider this. Suppose this is our main table:
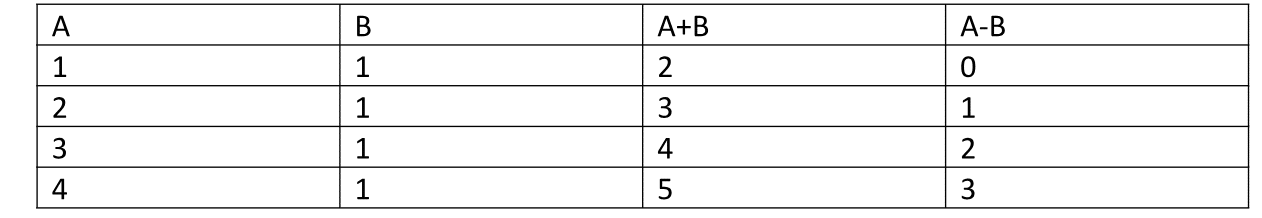
Now, if we were to partition this table vertically:
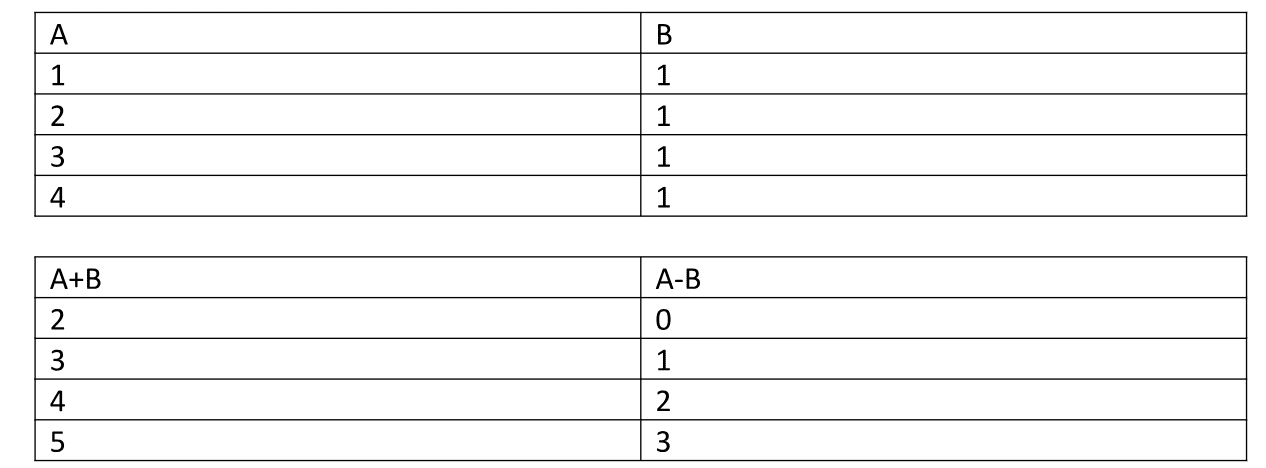
You see what happens? When you vertically partition a table they tend to become two completely different tables altogether.
However, if we were to partition them horizontally:
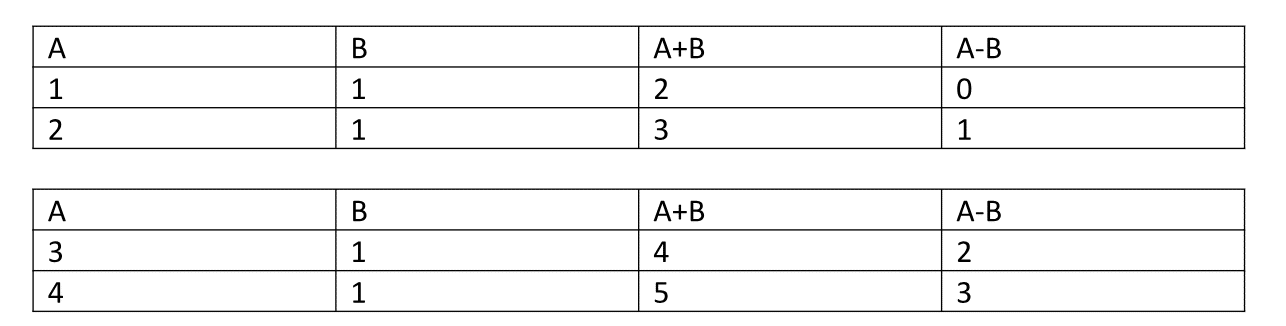
You see? It is the same table/database but with lesser data. These smaller databases are known as shards of the larger database. Each shard should be identical with the same table structure.
So what will happen if we do implement sharding in a POW protocol?
Sharding will make processing faster by splitting a state into different shards. However, if we are using POW, the smaller shards will be in danger of being taken over by malicious miners because of its low hash rate. In fact, this is the biggest reason why POW blockchains can never implement sharding, any and all small shards can be easily taken over.
This risk is completely mitigated in POS since it doesn’t have the concept of mining.
Conclusion
As you can see, things are going to change immensely once Proof of Stake is implemented. However, anyone who wants to enter the POW mining game in Ethereum still has ample of time to do so.

